If you’re a connoisseur of crypto compliance and KYC regulations, you likely expect and protect yourself from outright theft and fraud…but what about the risks that users are facing? In addition to theft and fraud, both of which reached record highs in 2024, the recent uptick in crypto-linked violent crime is also extremely concerning.
Multiple people have reported kidnappings, all in the name of blockchain – so where did the system go wrong? Did companies fail to meet KYC regulations for their custodial wallets, leaving users unprotected? Did users leave their self-hosted wallets open for attack? Or is something more sinister at play?
In today’s booming blockchain economy, no one can afford to gamble with their online safety. The fact that you’re a growing brand or an individual doesn’t matter to cybercriminals; once your crypto stash hits their radar, your only saving grace will be an identity verification system built specifically to handle KYC for crypto.
As experts in the field of identity verification, we hope you’ll make the choice to seamlessly integrate our signature BlueAssure platform into your policy and stop crypto crimes in their tracks, but even if you don’t, these are our best tips on how to stay one step ahead in today’s intricate blockchain identity verification game.

Your KYC-for-Crypto Basics
To mitigate future crypto compliance violations, blockchain identity verification breaches, and any other strike a criminal might launch, let’s examine KYC in crypto more closely.
There are multiple ways that KYC in crypto is different from KYC in any other realm (because it is) alongside the risks of a lackluster KYC process (they’re massive).
- KYC in Crypto Is a Whole Different Beast
Three primary differences exist between KYC in crypto versus other sectors: decentralization, pseudonymity, and anonymity. Unlike traditional financial institutions operating within defined jurisdictions, crypto transactions utilize decentralized platforms. The industry is still beholden to crypto compliance regulations, but this lack of central control makes risk assessment more difficult. - The Challenges of Anonymity and Pseudonymity
The anonymous and pseudonymous nature of cryptocurrency wallets also creates barriers to blockchain identity verification. As the current crypto landscape stands, most currencies like Bitcoin and Ethereum mask users’ true identities behind crypto handles, but link privately to their wallet addresses, a practice that attempts to balance privacy with the KYC transparency needed to combat illicit activities.
Other cryptocurrencies like Zcash rely on anonymous, rather than pseudonymous, transactions by using various cryptographic techniques, or “privacy coins,” to obscure transaction details, making it difficult to trace transactions back to specific users. While anonymity is an added layer of real-world protection, it circumvents KYC in crypto to prioritize user privacy. - Risking It All With Rudimentary KYC
While KYC in crypto is a critical method of preventing fraud and financial crime, it inherently involves collecting sensitive personal information. If your KYC process isn’t evolving at a faster rate than the criminals it’s trying to stop, this data can easily be mishandled or leaked, leading to devastating outcomes like privacy violations, identity theft, and financial ruin.
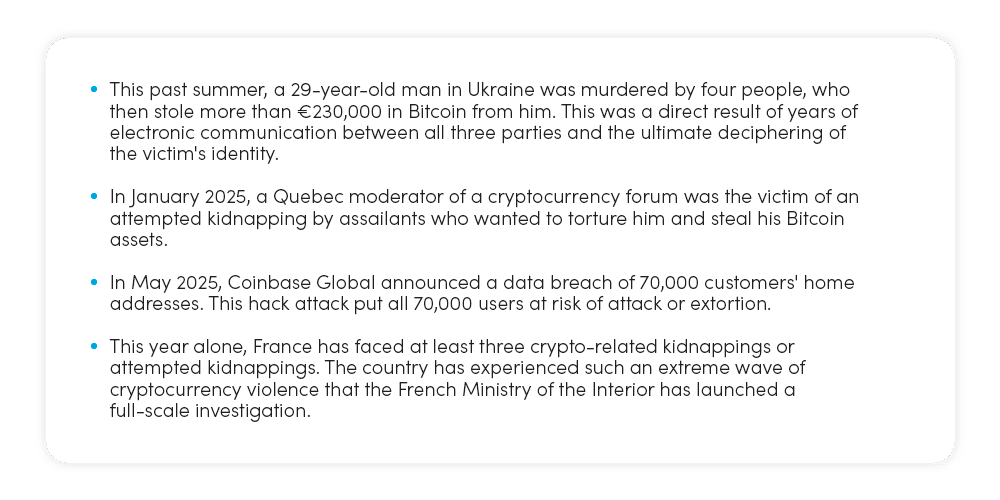
Sadly, the digital crimes mentioned above are only the tip of the crypto-attack iceberg: Recent incidents involving high-profile individuals illustrate how lackluster KYC in crypto can lead to real-world dangers like kidnapping and violent crimes due to poor verification controls, putting individuals at severe risk of financial and physical harm.
The Rise of Real-World Crypto Violence
As the price of bitcoin and other cryptocurrencies continue to surge, a new group of investors have joined the fray: extremely wealthy individuals. This uptick in affluent users means one thing: that anyone, from your well-to-do neighbor to the millionaire CEO of your favorite brand, is now a tempting target for criminals.
Just last month, two men were arraigned in New York for the kidnapping and 17-day-long gun, chainsaw, drug, and fire torture of a third party inside a luxury SoHo townhouse. Why? Because they wanted a man’s bitcoin password. Unfortunately, this violent scenario isn’t a one-off situation, even though most of the people who have been harmed in crypto-related crimes were well-educated in protective blockchain practices.
10 Tips To Protect Your Business from Crypto Attacks
Hopefully, these recent events have highlighted just how dire it is for every company to place their trust in only the most robust blockchain identity verification systems. KYC in crypto is an entirely different animal than Know Your Customer processes in other industries, and without it, you’re opening your brand up to endless criminal attacks and a massive loss of customer trust.
KYC regulations and procedures are more than legal formalities that maintain crypto compliance – when properly executed, they also serve as critical defenses against money laundering, fraud, and real-world violent crimes.

If you’re a business searching for better blockchain identity verification methods, here’s a checklist to follow.
- Maintain crypto compliance by conducting regular audits of your compliance frameworks.
- Collect and retain minimal information to meet KYC compliance.
- Invest in advanced cybersecurity solutions that rely on multi-factor authentication.
- Obtain customer consent before processing sensitive information.
- Anonymize or pseudonymize data when possible to protect user identities and maintain crypto compliance.
- Continuously monitor crypto transactions for red-flag activity.
- Educate employees on KYC-in-crypto best practices.
- Leverage AI and machine-learning algorithms for fraud detection and risk assessment.
- Keep detailed documentation of all KYC processes and data collection.
- Keep a pulse on evolving data privacy laws to ensure crypto compliance.

Block Future Blockchain Abusers With Our EVS Solutions
The list above is not only a helpful checklist to beef up your KYC in crypto, it also reflects the benefits you’ll gain by integrating our BlueAssure Cloud- or API-based products into your existing KYC policy. For years, EVS has honed its solutions to create the best possible suite of identity verification, fraud prevention, and risk mitigation products on today’s market. We do the heavy lifting to ensure our clients are meeting KYC regulations, maintaining crypto compliance, and keeping their reputations and their users safe. If crypto transactions are a part of your current or future business model, EVS and our BlueAssure platform are the swords you’ll want to wield against modern crypto crime. Reach out today to learn more about our comprehensive blockchain identity verification products and how they can mitigate or eliminate your company’s risk of becoming a crypto target.